Nexus Installation From Azure Registry to On-Premises
As part of various application deployment strategies, Nexus plays an important role in storing the artifact versions of various applications. In addition, using Nexus, we can store custom-built Docker images by configuring and creating a Nexus private registry.
Here, step by step, is how to create and configure the Nexus private registry.
We can install Nexus as a service or as a Docker container using Docker-Compose. In this setup, we are configuring Nexus as a Docker container.
Prerequisites
- Make sure Docker services are running and Docker-compose is working.
- Check to make sure the machine has at least 4 GB of RAM free, and
- Disk space of 10+ GB to store the Docker images.
Log in to the machine and select the directory. Then, create the Docker-compose file for Nexus
# cat docker-compose.yaml
version: "2
services:
nexus:
image: docker.io/sonatype/nexus3:3.20.1
restart: always
mem_limit: 3g
volumes:
- ./volume/nexus-data:/nexus-data
ports:
- "8081-8085:8081-8085"
- Nexus is configured with a memory limit of 3GB and storage is mapped to the VM for data and serves on port range of 8081 to 8085.
- Configured with a restart policy so that it restarts at the time the VM restarts.
The Nexus container may run with different permissions than the current user. Create the directory volume and set permission as below.
# mkdir volume
# chown -R 200 */volume
# chmod -R 777 */volume
Start the service using Docker-compose.
# docker-compose up -d
Docker-compose creates the containers and makes the services available for use on the following ports. Users will then be able to connect to and access these services.
:8081 -> Nexus UI served on http protocol
:8082 -> Nexus UI served on https protocol once configured
:8083 to 8085 -> Reserved for usage of individual repositories serving custom protocol such as Docker.
Note: In this case, (VM) refers to the virtual machine where your Nexus container is running.
Nexus, by default, serves the clients using http protocol, however, for security reasons, https protocol is used in serving the Nexus UI. In addition, some of the repository clients, such as Docker, need SSL-based communication, which needs https enabled in Nexus.
Follow these steps to create the certificates and configure Nexus to run with https.
1. Log in to the container using Bash.
$ docker exec -it -u root bash
2. Navigate to the below directory and create the keypair.
[root@ ]# cd /opt/sonatype/nexus/etc/ssl
[root@ ]# keytool -genkeypair -keystore keystore.jks -storepass changeit -keypass changeit -alias jetty -keyalg RSA -keysize 2048 -validity 5000 -dname "CN=,OU=Example, O=Sonatype, L=Unspecified, ST=Unspecified, C=US" -ext "SAN=DNS:,IP:" -ext "BC=ca:true"
After substitution, the values at the command look like this:
[root@ ]# keytool -genkeypair -keystore keystore.jks -storepass changeit -keypass changeit -alias jetty -keyalg RSA -keysize 2048 -validity 5000 -dname "CN=fcclnode3,OU=Example, O=Sonatype, L=Unspecified, ST=Unspecified, C=US" -ext "SAN=DNS:fcclnode3,IP:192.168.131.125" -ext "BC=ca:true"
3. Change the passwords in the https configuration file:
[root@ ]# cd ../jetty/
[root@ ]# vi jetty-https.xml
……………
/keystore.jks
changeit
changeit
changeit
4. Generate/link nexus.properties, in case it is not present.
[root@ ]# cd ..
[root@ ]# pwd
/opt/sonatype/nexus/etc
[root@ ]# ls
fabric jetty karaf logback nexus-default.properties ssl
[root@ ]# cp nexus-default.properties nexus.properties
5. Add the ssl port and include the https configuration file.
[root@ ]# vi nexus.properties
# Jetty section
application-port=8081
application-port-ssl=8082
application-host=0.0.0.0
nexus-args=${jetty.etc}/jetty.xml,${jetty.etc}/jetty-http.xml,${jetty.etc}/jetty-https.xml,${jetty.etc}/jetty-requestlog.xml
nexus-context-path=/${NEXUS_CONTEXT}
# Nexus section
nexus-edition=nexus-pro-edition
nexus-features=\
nexus-pro-feature
nexus.clustered=false
[root@ ]#exit
6. Stop and start the container for the changes to reflect.
# docker stop
# docker start
7. Verify the https connectivity is working and collect the certificate
# keytool -printcert -sslserver :8082 -rfc
Here, use the keytool to get the certificate we need to use 8082 to print the certificate.
Now, let’s check how the Docker proxy repo works by proxying Azure container registry (ACR) to the locally configured Nexus proxy repository.
Docker Proxy Repository Configuration and Certificate Configuration in On-Premises Machine
Prerequisite:
- Azure container registry (ACR) should be configured.
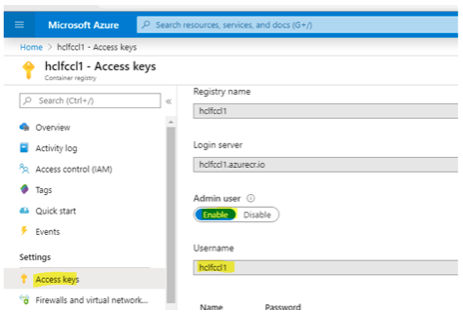
- Collect the ACR URL, username and password for configuration.
The above image shows the sample Azure container registry which is used to proxy the images to the on-prem Nexus registry running as a container.
Log in to Nexus in the browser using <VM IP>:8081, default username and password, which is admin/admin123.
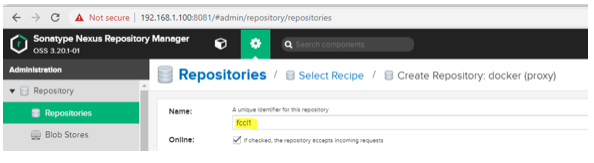
Select the Settings wheel at the top; then Repositories on the left side to create the repository, as shown below.
Follow the steps to configure the docker proxy repo.
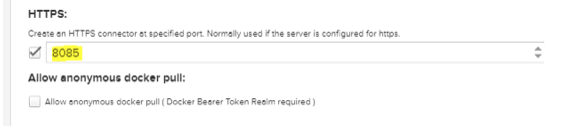
Select one of the remaining ports in the range of 8083 to 8085.
Provide the Azure container registry URL in the remote storage section as shown below.
Provide the ACR repository credentials as shown below.
The Docker proxy repository is now configured, and is pointing to the ACR for Docker images.
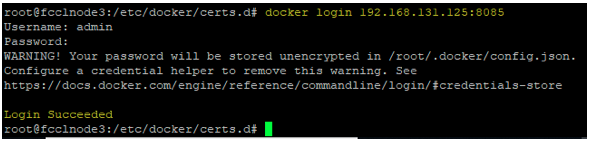
The following steps need to be configured in the VM where Nexus is running to integrate the Nexus proxy repository and the VM.
- Store the server certificate of Nexus in the docker certificate directory as below.
# cd /etc/docker/certs.d/
# mkdir :8085
# cd :8085
# keytool -printcert -sslserver :8082 -rfc > ca.crt
Example:
# keytool -printcert -sslserver 192.168.131.125:8082 -rfc > ca.crt
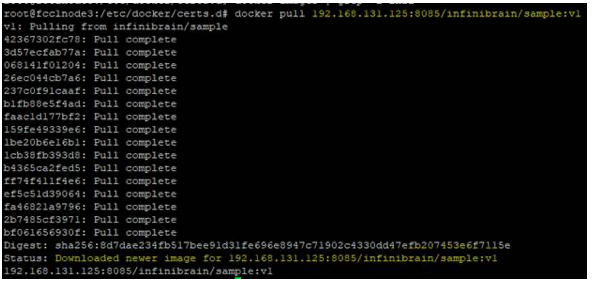
Pulling images from Proxy Repo
- After creating the proxy repository and configuring the certificates, the proxy is ready to pull the images.
- Initiate the pull operation and check that the images from the ACR registry are mirroring to the local Nexus repo.
Docker pull <proxynexusurl>:8085/<image name>:<tagname>
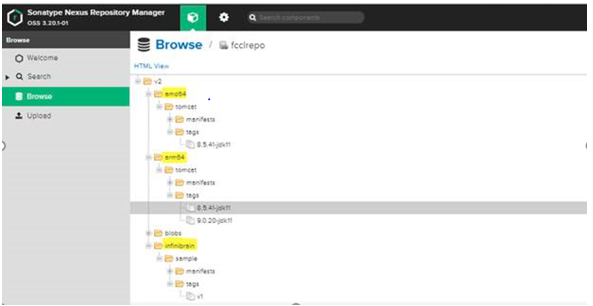
On the local Nexus UI, mirrored images will appear whenever the pull operation is successful. We have the following images mirrored from the Azure ACR.
Now, replication of ACR images is done using proxy repository.