Sysdig Brings Native Microsegmentation to Kubernetes Clusters
Sysdig today at the online KubeCon + CloudNativeCon North America 2020 conference announced it has added zero-touch network security that leverages its core runtime security software to microsegment Kubernetes networks.
Janet Matsuda, chief marketing officer for Sysdig, says this zero-trust network security for Kubernetes capability will be available free of charge to any IT organization that licenses Sysdig Enterprise.
The offering makes it possible to microsegment a Kubernetes environment in a matter of hours using controls that are native to Kubernetes at the namespace and service level versus relying on legacy firewalls to segment a cluster.
Sysdig is now automatically enforcing least privilege policies based on observed traffic and application and Kubernetes metadata it collects. That approach makes it easier to accurately implement network policies that are not overly permissive without breaking applications, notes Matsuda.
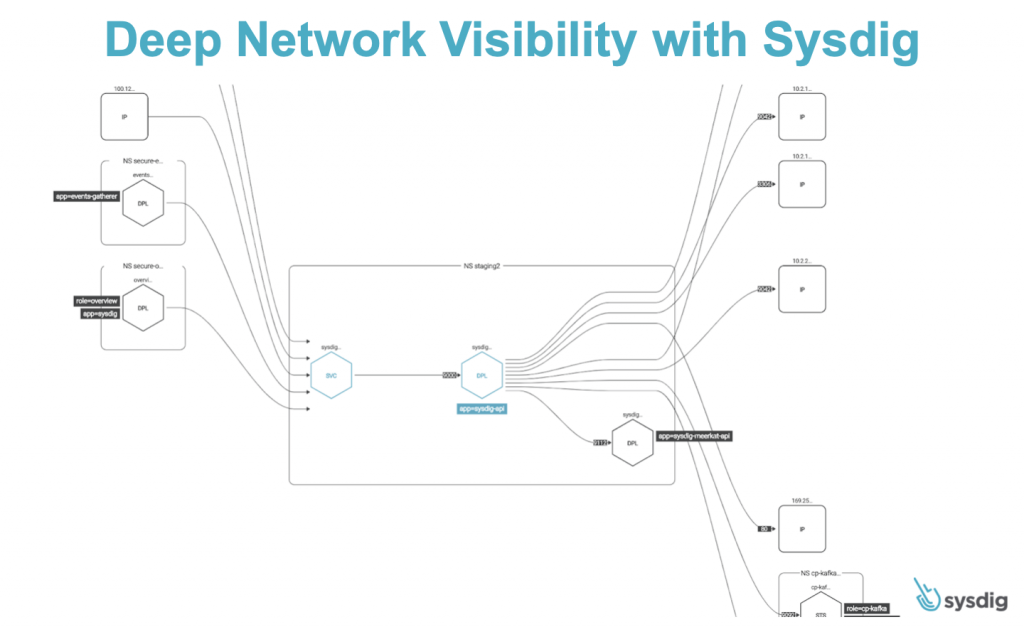
Sysdig is also adding dynamic network topology maps to visualize all communication into and out of a particular pod, service and application. This detailed visibility allows IT teams to more easily identify attempts to exploit overly permissive network policies.
There’s also now a Sysdig Audit Tap capability that can be used to fingerprint every process connection, including every network connection attempt. That capability is critical because it enables IT teams to identify unsuccessful connection attempts that might warrant further investigation using security information event management (SIEM) platforms.
In general, Matsuda says Sysdig is providing a more intuitive approach to microsegmentation in Kubernetes environments, which ultimately makes it easier to achieve compliance with various regulations or standards.
Microsegmentation using firewalls has been deployed on virtual machines now in legacy IT environments for several years. That approach keeps malware from moving laterally across the environment should any virtual network segment be compromised.
Historically, however, microsegmentation is difficult to manage and maintain as application environments evolve. Kubernetes environments make it even more challenging because of all the settings that IT teams are expected to master. It’s not uncommon for application teams to prefer to have their own cluster environment simply because managing multiple applications on a Kubernetes cluster is difficult. That said, multiple applications spanning running on different clusters eventually need to be networked.
It remains to be seen how easily microsegmentation might be enforced across application environments made up of microservices, which often have a lot of dependencies. The Sysdig approach relies on its ability to observe traffic flows to help determine how policies should be implemented as the application environment changes. In theory, that approach should advance best DevSecOps practices as microsegmentation becomes increasingly automated.
Regardless of the approach to Kubernetes security, as the platform itself becomes more widely employed the number of sophisticated cyberattacks being launched against it is increasing noticeably.