Qualys Secures Containers Using Lightweight Agent
Qualys today announced Container Runtime Security, a new approach to securing containers that makes use of functions to enable agent software that applies security policies to be embedded within a container.
Sumedh Thakar, president and chief product officer for Qualys, says this capability makes it possible for security policies to be applied to a container regardless of where it ultimately runs. This lightweight approach to securing container runtimes, he says, eliminates the need to rely on sidecars or privileged containers that are cumbersome to implement and manage.
In addition to blocking containers from being instantiated based on container runtime behavior, IT teams using Qualys Runtime Container Security can monitor file access in real-time via the Qualys Cloud Platform. IT teams can also apply network microsegmentation, vulnerability and exploit mitigation and virtual patching.
IT teams can create granular custom behavioral policies via a built-in policy library. Policies can also be added based on the behavior of containers observed over time.
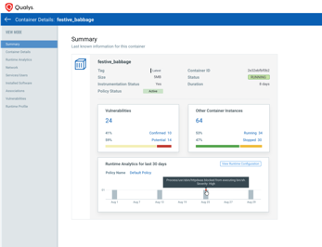 Thakar says Qualys Runtime Container Security advances DevSecOps via integration with continuous integration/continuous delivery (CI/CD) platforms. Policies injected into software builds will follow the image wherever it runs. IT teams can also immediately detect containers that are drifting from their parent images, which he says is typically an indication of a security risk being created as vulnerabilities are inadvertently or purposefully added to a container image or simple misconfiguration errors are made.
Thakar says Qualys Runtime Container Security advances DevSecOps via integration with continuous integration/continuous delivery (CI/CD) platforms. Policies injected into software builds will follow the image wherever it runs. IT teams can also immediately detect containers that are drifting from their parent images, which he says is typically an indication of a security risk being created as vulnerabilities are inadvertently or purposefully added to a container image or simple misconfiguration errors are made.
Qualys has previously committed to extending the reach of its cloud platform for detecting vulnerabilities to include endpoint detection and response (EDR), incident management capabilities and compliance tools using a single agent that can be deployed and managed centrally. In that context, containers are essentially now just another type of endpoint that can be managed and secured via Qualys Cloud Platform, Thakar says.
Most security policies will continue to be defined by IT security teams; however, Qualys Runtime Container Security will make it easier for DevOps teams to implement those policies, he notes.
Just as importantly, he adds, IT security teams will be able to more easily apply the same security policies employed across the rest of the IT environment to containers.
Historically, IT teams have relied on agent software to enforce policies across a broad swath of assets. Containers required a different approach up until now because they required agent software to attached to them because otherwise, the container would become too large. Functions are self-contained modules of code that perform specific tasks. They are being used most widely to enable developers to invoke serverless computing frameworks.
Regardless of the approach, securing containers has become a pressing issue as the number of container applications being deployed in production environments continues to expand rapidly. It’s too early to say to what degree IT teams might shift to an approach that embeds agent software directly into containers. However, it’s already apparent there is a need to reduce the current level of complexity around securing containers.




