Prevasio Previews Container Security Service
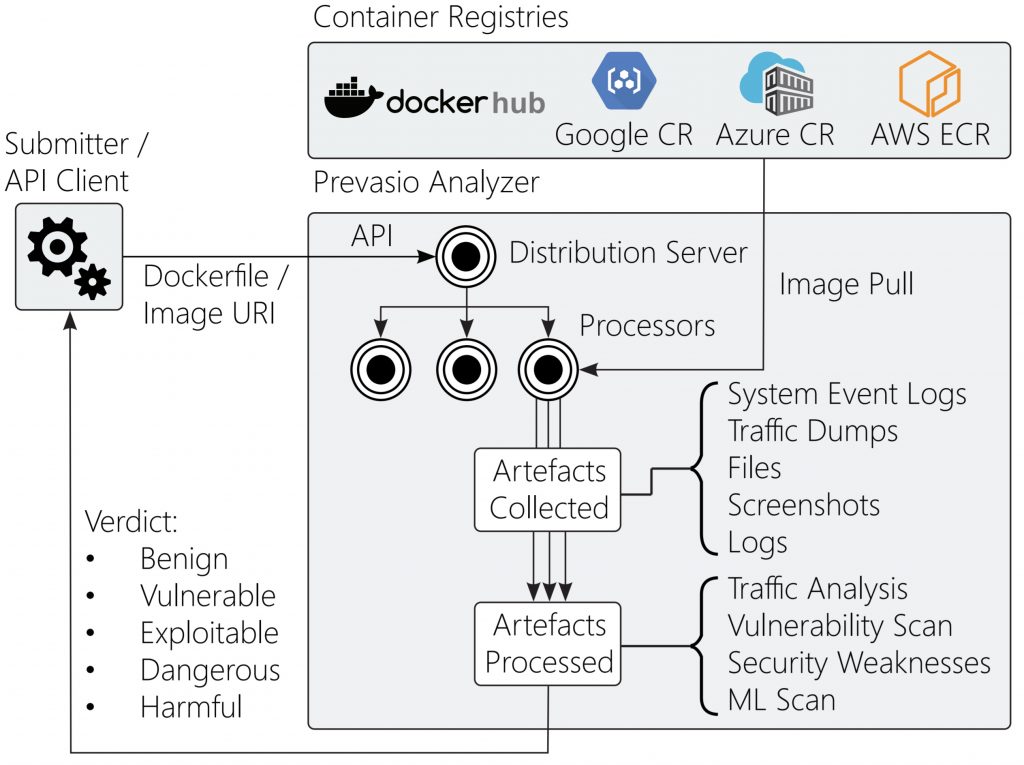
Prevasio is providing early access to a namesake container security service that intercepts and inspects all network traffic generated by containers, including HTTPS traffic, and then applies machine learning algorithms to surface vulnerabilities.
Company CEO Rony Moshkovitch says the artificial intelligence (AI) models created by Prevasio has been trained to identify tens of thousands of malicious and bespoke files, based not only on static file characteristics but also on the disassembled code and its sequence. Those AI models were trained using the more than 3.5 million containers readily accessible on public clouds.
Initially, the Prevasio container security service runs a container scan using the Trivy Vulnerability Scanner from Aqua Security to identify any packages with known vulnerabilities that previously were reported. SSL/TLS inspection is then enabled using a MITM proxy certificate that is injected dynamically into any container to decrypt traffic.
Prevasio also makes available an automated penetration test that simulates attacks by first trying to fingerprint running services and then engaging exploits against them. In addition, Prevasio can launch a brute-force attack against an identified service such as SSH or MySQL to find weak credentials.
It also collects kernel-level system events that are visually displayed in the form of a force-directed graph to surface problematic containers and quickly establish remote access points.
Finally, Pervasio will generate a report that identifies weak/clear-text passwords, GitHub repositories and ports/services that might be exposed.
Moshkovitch says the Pervasio container security service can be accessed via application programming interfaces (APIs) and command-line interfaces as part of a DevSecOps process or via a graphical user interface (GUI), which might appeal more to a traditional cybersecurity team.
Regardless of the approach, Moshkovitch says it’s becoming increasingly apparent DevOps teams would rather invoke a service to scan containers rather than set up all the tools and required infrastructure themselves. In fact, he notes one of the reasons why not much progress has been made in advancing DevSecOps practices is because previously cybersecurity teams were counting on DevOps teams to set up all the required tooling.
Developers, meanwhile, often feel they are being held more accountable for application security, yet they don’t have the tools they need to address the issue.
It’s not clear yet to what degree container scanning services might positively impact the adoption of best DevSecOps practices. Each organization will need to define its own practices. It’s also quite probable many developers will take advantage of container security scanning services as a way to avoid having to engage cybersecurity teams later. After all, the DevSecOps goal has always been to accelerate the development of secure applications. One way to achieve that goal is to minimize the involvement of cybersecurity professionals in the DevSecOps processes as much as possible.
Naturally, cybersecurity teams may need some time to adjust to that new reality. However, given all the tasks they already have at hand, it may not take all that long for most of them to adjust.