Nubeva Rises to Cloud-Native Encryption Challenge
Nubeva Technologies has extended the network decryption software it developed for the Trusted Layer Security (TLS) encryption protocol to application workloads based on containers and Kubernetes clusters.
Steve Perkins, chief marketing officer for Nubeva, says cloud service providers now require IT organizations to use TLS, a cryptographic protocol accepted the Internet Engineering Task Force (IETF) to secure their applications in place of the Secure Socket Layer (SSL) protocol. However, DevOps teams deploying cloud-native applications based on containers and Kubernetes presently lack visibility into applications encrypted using TLS.
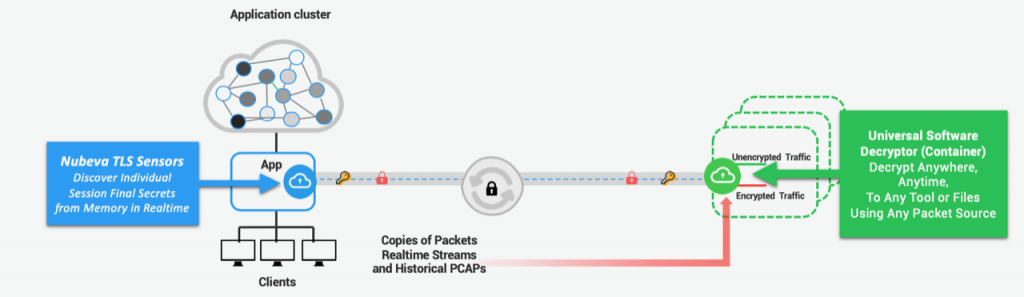
Nubeva TLS 1.3 Decrypt obtains the keys from any north/south or east/west session to provide visibility into traffic running in and out of containers to enable both real-time monitoring and forensics of Kubernetes deployments, including variants of Kubernetes such as Amazon Elastic Kubernetes Service (Amazon EKS), Azure Kubernetes Service (AKS) and Google Kubernetes Environment (GKE), Perkins says.
The encryption keys are discovered and extracted from certificates using a Symmetric Key Intercept architecture that inserts agent software running in memory which employs signatures infused with machine learning algorithms to decrypt traffic. Once the keys are stored, users can decrypt the encrypted data in motion at scale, Perkins says. Nubeva claims the key extraction agent consumes less than 1% of compute resources on a single CPU core for all the workloads on a node configured with a few megabytes of memory. Because Nubeva runs in user space, it’s completely platform-independent, he adds.
Perkins says up until now organizations that have embraced encryption have had to sacrifice observability and are completely blind. Nubeva TLS 1.3 solves that problem using an out-of-band approach versus a more traditional “man-in-the-middle” legacy approach that no longer works when organizations employ TLS, he says.
Nubeva TLS 1.3 is also designed to work with any packet capture and broker system, including AWS Virtual Private Clouds (VPC) traffic mirroring and Azure VTAPS. Additionally, it is compatible with TCPdump and PCAP files, as well as mass storage of PCAPs that require selective or bulk decryption.
At a time when cloud service providers such as AWS are driving an “Encrypt Everything” initiative that seeks to make cloud-native applications running on their platforms more secure, the need to observe application traffic has resulted in many organizations opting not to embrace TLS even though it is a more secure cryptographic protocol. However, as the speed at which TLS traffic can be decrypted improves, the chances that more applications will be encrypted both in the cloud and in on-premises IT environments increase. In fact, it’s arguable true hybrid cloud computing will never achieve mainstream adoption without first solving this encryption challenge.
Not too long ago, encryption was applied only to an organization’s most sensitive applications because of all the overhead associated with encrypting and decrypting data. However, now that compute power is comparatively inexpensive, encryption has become more affordable. The challenge now is finding a way to employ encryption effectively without violating one the primary observability tenets of DevOps.