NeuVector Melds Container Compliance, Security
NeuVector, at the online KubeCon + CloudNativeCon Europe 2020 event, announced it has updated its namesake container security platform to make it simpler to address compliance requirements.
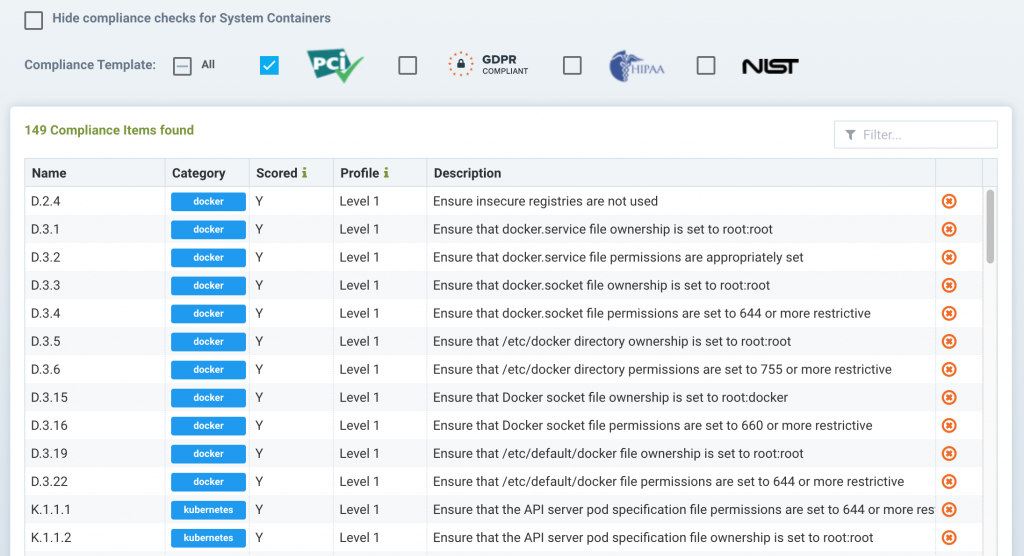
The latest version of NeuVector enforces Payment Card Industry Data Security Standards (PCI DSS) and General Data Protection Rule (GDPR) controls in addition to providing workflows that make it easier to track known vulnerabilities.
NeuVector is adding support for open source Open Policy Agent (OPA) software to simplify implementing compliance controls as code. Now being developed under the auspices of the Cloud Native Computing Foundation (CNCF), support for OPA within NeuVector makes it possible to review and query NeuVector security policies within a Kubernetes cluster.
In addition, NeuVector has added built-in reporting tools intended to make it easier for IT teams to facilitate audits of container applications and added more granular role-based access controls (RBACs) for use in environments where multiple types of IT administrators may need to access the platform.
Finally, NeuVector has expanded its leading vulnerability scanning and risk assessment capabilities to include support for the AWS Lambda serverless computing platform. Via the open source Serverless integrated development environment (IDE), DevOps teams can trigger vulnerability scanning on AWS Lambda serverless functions written in Java, Node.js, Python or Ruby. NeuVector analyzes the AWS permissions granted for each function for policy violations and embedded secrets.
Glen Kosaka, vice president of product management for NeuVector, says IT teams should expect the company to add support for additional regulatory standards based on demand. As best DevSecOps practices continue to evolve, it’s apparent that responsibility for implementing a wide range of compliance controls is shifting further left toward developers, he notes.
The challenge is making it easier for developers to address compliance requirements within a larger DevSecOps workflow, Kosaka adds. As such, the process of implementing security and compliance controls needs to converge within the context of a single platform.
While it’s still early days as far as adoption of best DevSecOps practices is concerned, Kosaka says the chronic shortage of cybersecurity professionals is likely to force the issue sooner than later. The rate at which applications are now being developed is occurring is simply too fast for cybersecurity teams to review before code is promoted into a production environment. As such, developers need to assume more responsibility for making sure the right controls are in place, says Kosaka, adding cybersecurity teams will still need to verify those controls are in place.
The rate at which organizations embrace best DevSecOps practices naturally will vary depending on the culture of the organization. Developers have a vested interest in making sure security and compliance issues are addressed as early as possible. After all, it’s not like security and compliance issues will go away. They will just be added to a long list of other issues that need to be addressed once developers start debugging an application. As always, an ounce of prevention is always going to be worth a lot more than a pound of cure applied after an application has already been deployed.