Establishing a Kubernetes Pod Security Policy
Kube-PSP-Advisor is a tool that makes it easier to create K8s Pod Security Policies (PSPs) from either a live K8s environment or from a single. yaml file containing a pod specification (deployment, daemon set, pod, etc.).
What is a Pod Security Policy?
A pod security policy is a cluster-level resource that controls security sensitive aspects of the pod specification. The PodSecurityPolicy objects define a set of conditions that a pod must run with to be accepted into the system, as well as defaults for the related fields. They allow an administrator to control the following:
PSPs allow you to control:
- The ability to run privileged containers and control privilege escalation
- Access to host file systems
- Usage of volume types
- Usage of host networking and ports
- And a few other aspects including AppArmor, sysctl and seccomp profiles
Enabling Pod Security Policies
We are going to create two policies:
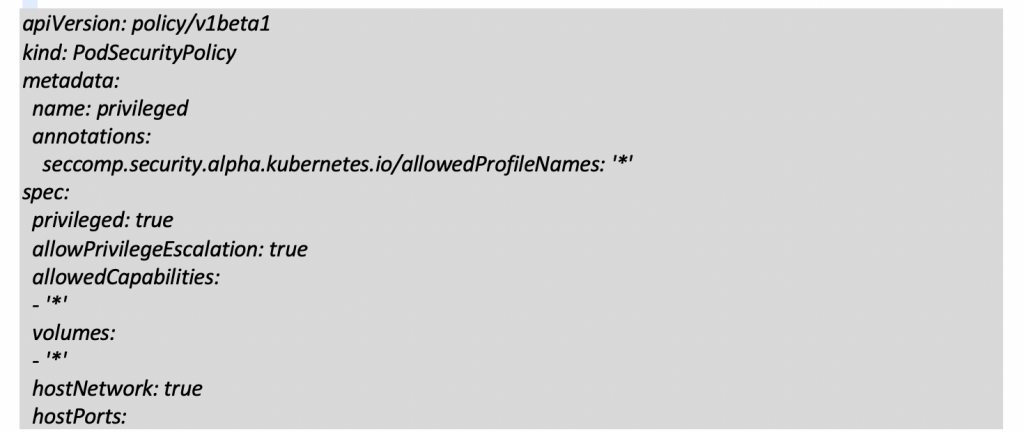
Privileged
This policy will be implicitly accessible to cluster admins and chosen by default since they have access to all resources. This policy is the least restrictive you can create.
To create it:
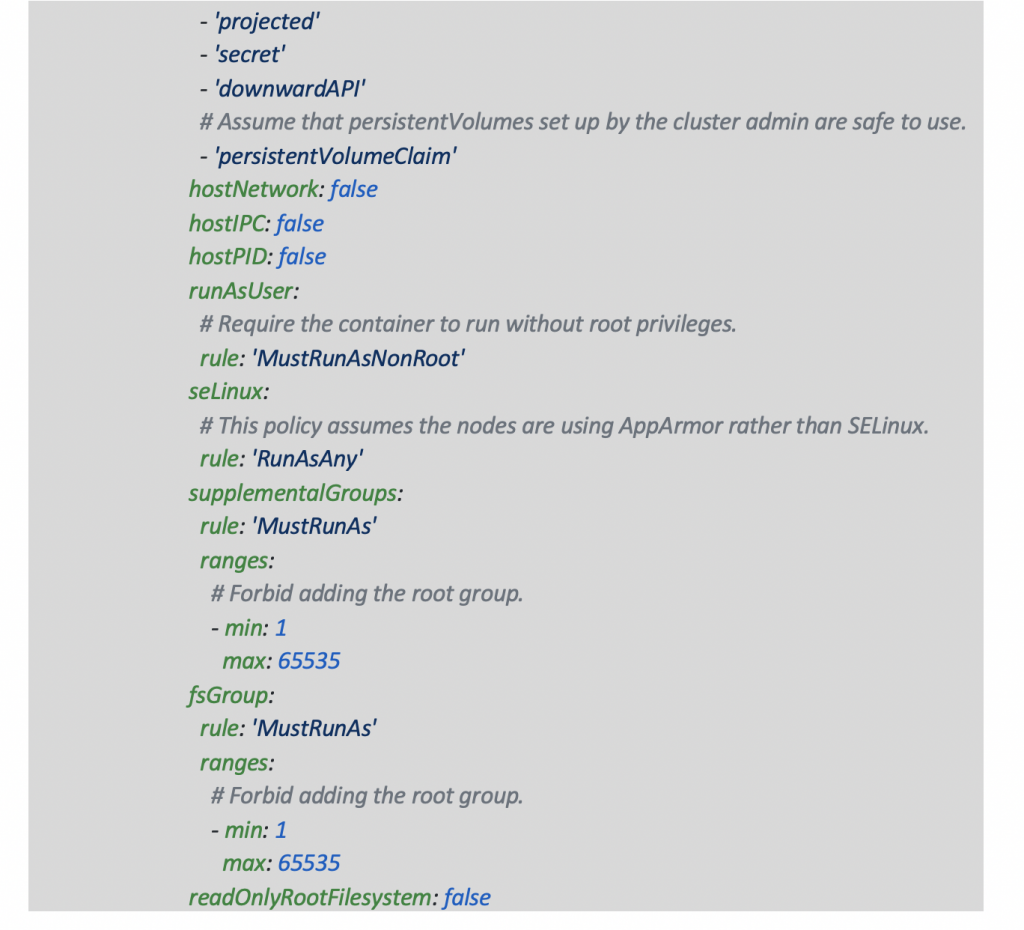
Restricted
This policy we will explicitly assign to all authenticated users. It denies running as root or escalating to root, requires a security profile, limits volume types, and a few other aspects.
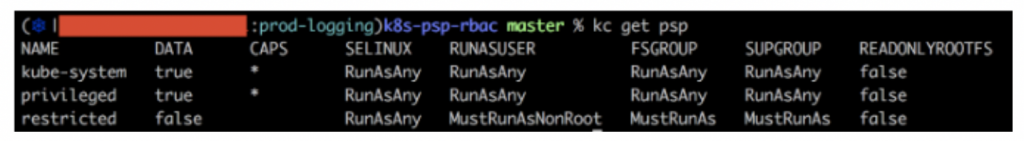
You should now have (at least) two pod security policies. Run kubectl get psp and you should see output similar to the following:
Kubernetes Pod Security Policy Best Practices and Challenges of Implementing in Production
We all know the theory of kubernetes security best practices:
- Do not run privileged containers.
- Do not run containers as root.
- Do not allow access to the host namespace.
- Restrict Linux capabilities.
Conclusion
Building a Kubernetes Pod Security Policy can be difficult. Not all applications might work following all the Kubernetes security best practices by the book. That doesn’t mean that you should ignore and skip implementing PSP at all. If a specific pod requires some additional access, still being able to implement a PSP that restricts further access privileges is definitely a good security approach. This is actually something that you will find in most production environments.
kube-psp-advisor makes implementing Kubernetes Pod Security Policy a simple and straightforward process, so you can get running in almost no time, adapting to your application requirements and specifically fine-grained for each one to allow only the least access privilege.
Containers and orchestrators are not inherently more or less secure than traditional virtualization technologies. If anything, I think containers and orchestrators have the potential to revolutionize the security industry and truly enable security at the speed of DevOps.