CloudBees Leverages Docker Containers to Harden CI Platform
CloudBees has made available a hardened version of its continuous integration (CI) platform that makes use of Docker containers to comply with specifications defined by the U.S. Department of Defense (DoD).
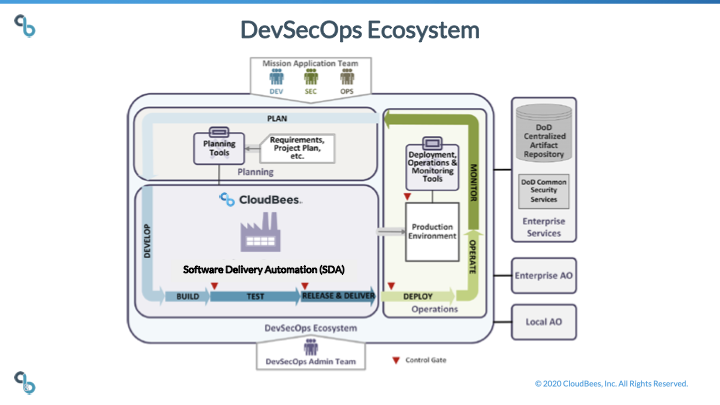
Michael Wright, director of the federal sector at CloudBees, says CloudBees CI, formerly known as CloudBees Core, is based on a container that has achieved a Certificate to Field (CTF) from the U.S. Air Force Platform One team, which is defining DevSecOps requirements for the entire DoD. Software containers that receive a CtF can be used to deploy a platform within an IT environment that has received an Authority to Operate (ATO) certification under guidelines defined by the Defense Information Systems Agency (DISA) and the National Institute of Standards and Technology (NIST).
CloudBees CI is based on the open source Jenkins platform, which comes in the form of a hardened Docker container image that can be accessed via a Department of Defense Centralized Artifact Repository (DCAR) repository. That image minimizes the use of any libraries or components that have known security vulnerabilities. If, for example, a team uses a library to execute http communication between a CloudBees CI master and agent, CloudBees CI automatically ensures secure ports and protocols are used at both ends. DevOps teams from any DoD or civilian agency can pull the hardened Docker container image provided by CloudBees out of DCAR.
Wright says that in addition to government agencies, any organization that builds software on behalf of government agencies should also be employing the hardened version of CloudBees CI. In fact, Wright notes that application development now routinely spans government agencies and private companies that need to comply with federal mandates.
In general, interest in hardened implementation of CI platforms is on the rise as organizations embrace best DevSecOps practices. Wright says the adoption of hardened CI platforms is now moving well beyond government agencies as organizations rather than reinvent the same wheel adopt specifications defined by the DoD and NIST.
That interest is also pushing more organizations to adopt a curated instance of Jenkins rather than simply downloading the open source Jenkins platform that is now being developed under the auspices of the Continuous Delivery Foundation (CDF), an arm of the Linux Foundation. While the CDF is driving the development of Jenkins, federal agencies and enterprise IT organizations typically require a level of commercial support that is provided by CloudBees.
Overall, being able to document control over a software supply chain has become both cybersecurity and compliance issues. Auditors increasingly are requiring organizations to produce reports that make it clear every module of code has been tested and vetted, a process that usually begins with making sure the repository from which that code was pulled is secure.
Of course, not every organization requires the same level of zeal when it comes to enforcing cybersecurity and compliance policies. However, as the adoption of best DevSecOps practices continues to grow, it’s now only a matter of time before more organizations look to harden the entire software development life cycle end to end.