Aqua Security Surfaces Attacks on Container Platforms
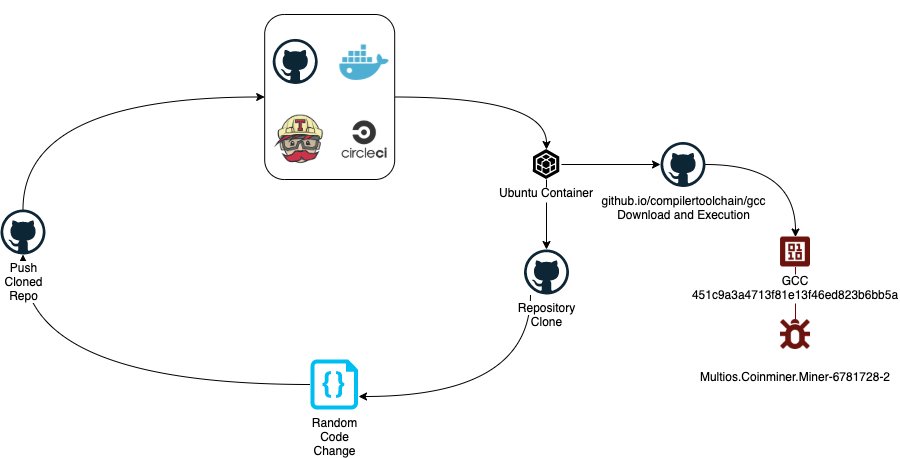
Aqua Security has discovered a wave of cybersecurity attacks that abuse automated build processes to hijack resources from software development environments such as Docker Hub, GitHub, Travis CI and Circle CI to mine cryptocurrencies.
Assaf Morag, lead data analyst at Aqua Security, says some of the attacks were traced to 11 GitHub accounts that were used to create 51 GitHub projects that were masquerading as popular software projects including nginx, okular, openssh, openvpn, seahorse, nautilus and zookeeper. At the same time, researchers over the course of a few hours also discovered 56 Docker Hub accounts also using the names of popular software. During the build process, these container images proceeded to download a cryptominer from a single GitHub repository.
For three days, Morag says, this campaign amassed more than 23,300 commits in GitHub and 5,800 builds in Docker Hub, translating into roughly 30,000 Monero mining sessions. All the images were set to download the same binary file labeled GCC. That file has now been marked as malicious, he notes, adding things would be if Docker Hub didn’t limit automated builds to a two-hour duration.
The campaign has also been extended to include Travis CI and Circle CI, which also make available software development platforms-as-a-cloud services.
In addition to increasing in volume, cyberattacks involving container technologies are becoming more sophisticated, Morag says. In the first half of 2020, there were on average 160 attacks per day against honeypots deployed by Aqua Security, which compares to an average of 11 attacks per day in the second half of 2019. Aqua Security also found between one and eight images were used each day with an average of he 2.75 images per day.
Aqua Security is also seeing cybercriminals implementing more advanced evasion techniques that elude basic security countermeasures such as static scanning, notes Morag.
As part of an effort to provide IT teams with more insights into those attacks Aqua Security has also published a list of classifications for attacks is discovering via its honeypots. Those attacks have been mapped to the MITRE ATT&CK framework, he no.
In general, Morag says many cybersecurity teams are underestimating the rate at which cybercriminals are developing exploits for containerized applications. They are also assuming that because many of these initial attacks are focused on cryptomining they don’t represent a lethal threat. However, what may appear to be little more than a nuisance today my very well turn out to be the same vector employed later to distribute more targeted attacks.
Regardless of severity, it’s clear cybercriminals are becoming more adept at exploiting containers. That’s a signal for organizations to embrace best DevSecOps practices before something more troubling occurs. In fact, it’s probable many cybercriminals already know a lot more about container technology than many of the IT organizations that are just now starting to deploy containers at scale.