Anchore Applies Container Image Scanning to DevSecOps
Anchore this week expanded the scope of integrations it provides organizations that adopt its container security platform as part of an effort to advance the adoption of best DevSecOps processes.
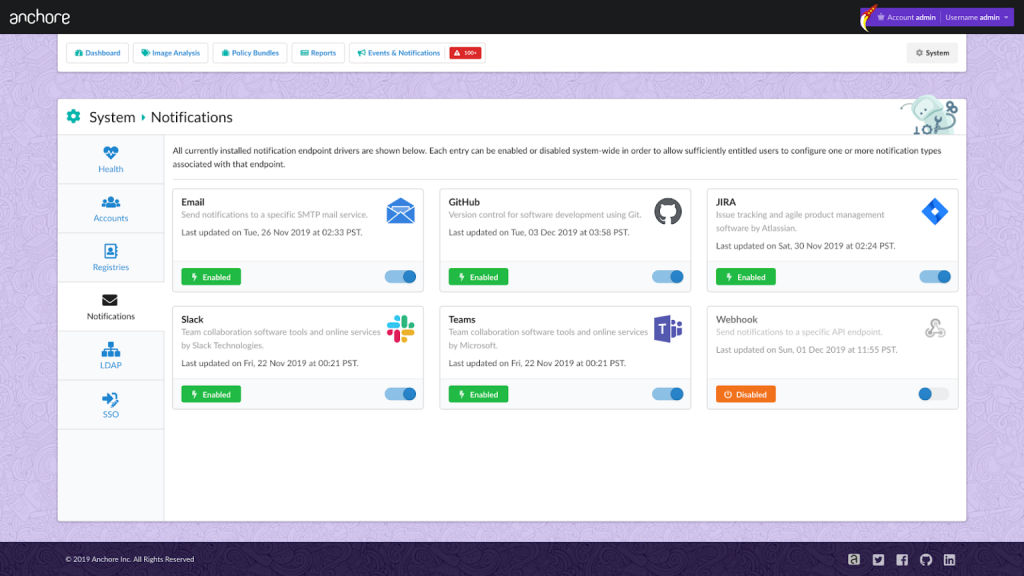
Ross Turk, vice president of marketing for Anchore, says version 2.2 of Anchore Enterprise, which is based on an open source engine for scanning containers, adds the ability to share notifications via email, webhooks or integrations with Slack, Jira, GitHub Issues and Microsoft Teams. The goal is to make it easier to create DevSecOps workflows spanning DevOps teams and cybersecurity professionals, he says. Earlier this year, Anchore announced the availability of Anchore Container Scan action for GitHub Actions.
Anchore also announced this week integration with Harbor, a container image registry being advanced under the auspices of the Cloud Native Computing Foundation (CNCF). IT teams now can scan container images stored in a registry as an alternative to scanning images as they are built using a continuous integration/continuous delivery (CI/CD) platform, says Turk. That option is needed because not every organization employing container images may have adopted a CI/CD platform, he notes.
 Anchore Engine goes beyond basic source and binary scanning of container images to also inspect configuration and contents of container images. The opportunity the company is pursuing now is to make it easier for organizations to make the scanning of container images part of the workflow that revolves around any container platform, Turk says.
Anchore Engine goes beyond basic source and binary scanning of container images to also inspect configuration and contents of container images. The opportunity the company is pursuing now is to make it easier for organizations to make the scanning of container images part of the workflow that revolves around any container platform, Turk says.
In general, Turk says containers represent something of a cybersecurity paradox. On the one hand, containerized applications might be less sure because containers that might contain vulnerabilities can be shared more indiscriminately. On the plus side, however, it’s much easier to rip and replace containers with known vulnerabilities than it is to patch a monolithic application. The degree to which containerized applications might be more secure than monolithic applications will come down to how proactive organizations are about implementing best DevSecOps practices, says Turk. In fact, he contends DevSecOps is not so much about platform and technologies as much as it about people, process and culture.
It remains to be seen to what degree the rise of containers and microservices will force organizations to embrace DevSecOps. Most organizations will recognize the inherent challenges associated with securing containerized applications. However, realigning responsibilities in a way that makes developers more accountable for ensuring vulnerable code doesn’t get packaged up in containers is a major challenge. At the same time, cybersecurity professionals will have to trust that developers are going to do the right thing in terms of scanning images before they are deployed in production environments. Cybersecurity teams may still want to verify those images are secure once they are deployed in a production environment, but they can’t slow down the application development process to scan every piece of code being deployed. Otherwise, as mountains of code awaiting a cybersecurity review will pile up and all the time and effort put into adopting containers and best DevOps practices will wind up being for naught.



