Anchore Adds To Container Security Toolbox
Anchore announced it is making available a series of open source container security tools that will make it possible to address a wide range of vulnerabilities long before an application is deployed in a production environment.
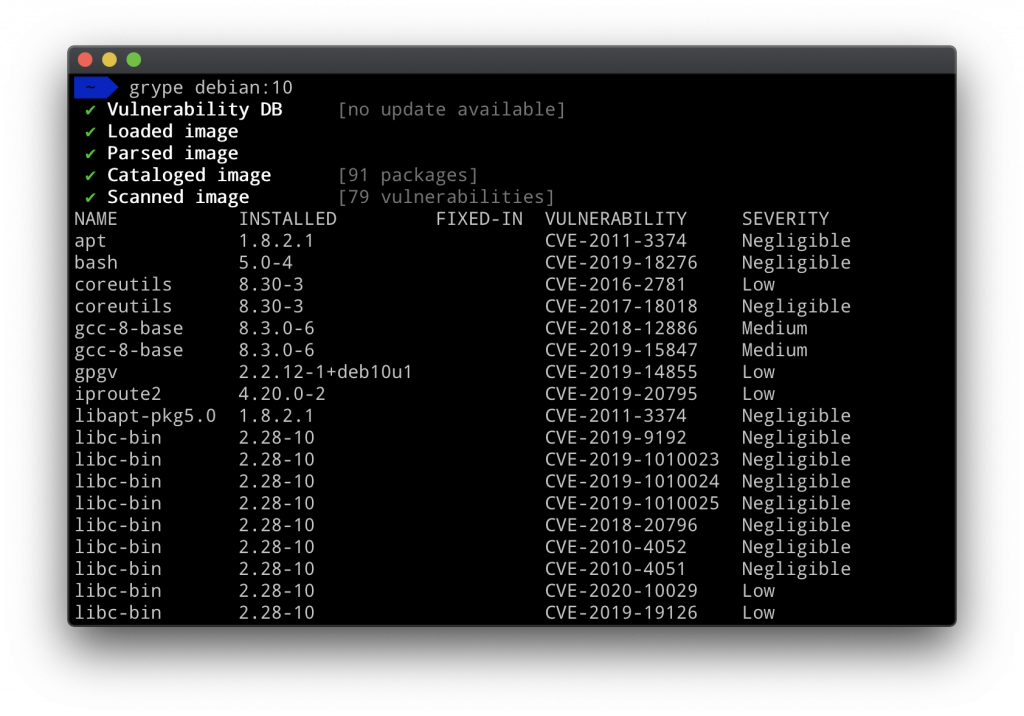
The first of two offerings in this series is Grype, which scans container images and files systems for known vulnerabilities using based on data compiled from the Anchore Feed Service and multiple public data sources. A Visual Studio Code extension for Grype is also available, and developers also can trigger a vulnerability scan of GitHub projects using the Anchore Container Scan from within Grype.
The second tool is Syft, which automatically creates a software bill of materials by analyzing container images and file systems. That software bill of materials makes it easier to ascertain what software components were employed to build a container image, which is critical in determining what vulnerabilities might be present.
 Neil Levine, vice president of products for Anchore, says the goal is to make it easier for developers to assume more responsibility for application security as part of a defense in-depth approach to implementing best DevSecOps practices. The tools for developers are intended to complement offerings from Anchore that secure runtimes and hosts.
Neil Levine, vice president of products for Anchore, says the goal is to make it easier for developers to assume more responsibility for application security as part of a defense in-depth approach to implementing best DevSecOps practices. The tools for developers are intended to complement offerings from Anchore that secure runtimes and hosts.
In general, Levine says just about every container application deployed has vulnerabilities for two reasons. For one, a lot of open source code isn’t vetted for all known vulnerabilities before it is encapsulated in a container. In addition, new vulnerabilities in open source code inevitably are discovered after a container application has been deployed. In the absence of a bill of materials, it becomes exceedingly challenging for IT organizations to determine what open source code was employed where, he says.
That bill of materials also plays a critical role in enabling organizations to determine the potential severity of the threat to their applications, Levine adds. Not all vulnerabilities pose the same level of threat. The bill of materials plays a crucial role in enabling organizations to prioritize their remediation efforts.
There is now no shortage of free security tools that developers can incorporate into their workflows to eliminate vulnerabilities in code before it is compiled in an application winding its way through a formal DevOps workflow. In theory, that approach should greatly reduce most known vulnerabilities. There are, however, vulnerabilities associated with runtimes that will be discovered by security tools that have been embedded within a continuous integration/continuous delivery (CI/CD) platform. IT teams should scan hosts for known vulnerabilities as well. As it turns out, most of the recent container vulnerabilities discovered focus on using malicious containers to take over an entire host, otherwise known as a “jailbreak.”
Regardless of the approach to container security, however, the best remediation process is the one that was never needed because the developers addressed a vulnerability before anyone knew it existed.




