10 Steps to Ensure PCI DSS-Compliant Container Deployment
Enterprises seeking to leverage containers and microservices in compliance with the Payment Card Industry Data Security Standard (PCI DSS) will find some advantageous synergies between the regulations and the technologies, as well as some aspects that require particularly careful attention. While PCI-DSS version 3.2, the industry’s latest, does not yet specifically address containerized environments, enterprises must nevertheless ensure that appropriate monitoring, security and governance is in place to achieve compliance. This is especially important, as recent reports are showing a struggle to maintain compliance.
Containers and microservices are inherently supportive of PCI DSS compliance across several fronts. In an ideal microservices architecture, each service and container deliver a single function, which is congruent with the PCI DSS requirement to implement only a single primary function with each server. In the same way, containers provide narrow functionality by design, meeting the PCI DSS mandate to enable only necessary protocols and services.
However, container environments raise PCI DSS compliance challenges in the areas of monitoring, establishing security controls and limiting the scope of the Cardholder Data Environment (CDE) with network segmentation. Because of containers’ ephemeral nature—spinning up and down quickly and dynamically, and often only existing for a number of minutes—monitoring and security solutions must be active in real-time and able to automatically respond to rapidly transforming attacks.
Because most container traffic is internal “east-west” communication between containers, traditional firewalls and security systems designed to vet north-south traffic are blind to nefarious threats that may escalate within the container environment. And, the use of containers can actually increase the CDE, requiring critical protections to the size of the entire microservices environment unless limited by a container firewall able to fully visualize and tightly control its scope.
A ‘knee-jerk’ reaction could be to physically separate container environments that are in-scope, but this can severely restrict modern automated DevOps CI/CD pipelines and result in slower release cycles and underutilized resources. However, cloud-native container firewalls are emerging that provide the required network segmentation without the sacrifice of the business benefits of containers.
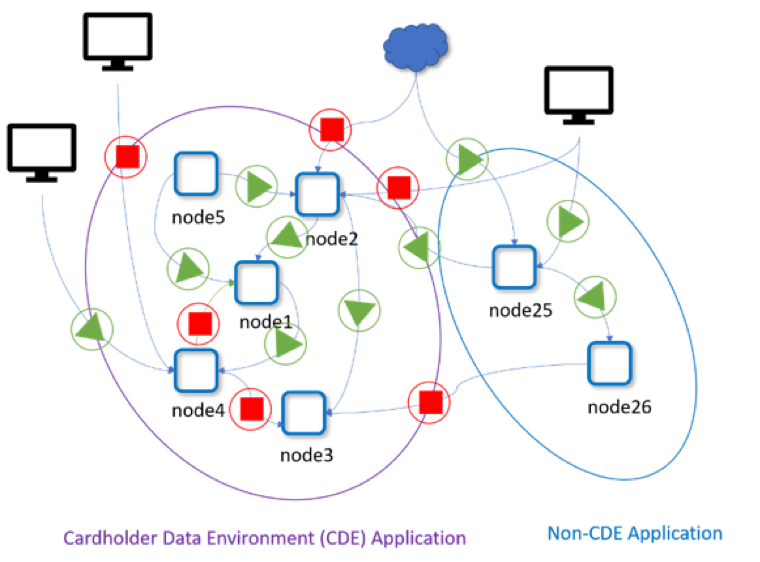
These are the 10 PCI DSS requirements that apply to organizations relying on microservices and containers, and how best to adhere to them:
1) Install and maintain a firewall configuration to protect cardholder data (PCI DSS 1.2, 1.3)
Among other details, PCI DSS compliance requires a current network diagram that identifies all connections between the CDE and other networks, and the flow of all cardholder data. PCI DSS sections 1.2 and 1.3 call for using a firewall to segment in-scope CDE traffic from all other connections. This means denying all connections and traffic that are not necessary to the CDE and prohibiting direct public access to the CDE.
In traditional environments, achieving this segmentation would mean utilizing separate networks protected by traditional firewalls. However, applying the same approach to protect cloud-native applications would increase friction in CI/CD and deployment pipelines, add to costs and make resource utilization across clusters less efficient. Ultimately, the traditional approach would severely impact and reduce benefits intrinsic to container environments.
For these reasons, container environments should meet these requirements by relying on a container firewall designed to automatically discover, monitor and protect all elements and data flows within the environment in real-time. The container firewall must also provide microsegmentation between CDE and non-CDE workloads and policies to restrict internal and external CDE connections as appropriate.
2) Do not use vendor-supplied defaults for system passwords and other security parameters (PCI DSS 2.1)
Businesses are required to change security defaults and default accounts, use industry-accepted hardening standards, strongly encrypt non-console admin access and keep an inventory of system components within the PCI DSS’s scope. To secure container environments in line with these requirements, utilize tools that detect and provide alerts for defaults in need of change. Run Docker Bench security and Kubernetes CIS Benchmarks reports to meet accepted standards and harden the environment. Use encryption alongside tools that identify and block non-encrypted traffic from establishing CDE connections. Customized compliance checks can also be conducted on hosts as well as containers to verify security parameters.
3) Protect stored cardholder data (PCI DSS 3.1-3.7)
PCI DSS requires the use of strong and secure cryptographic keys to encrypt cardholder data, as well as careful document restrictions and procedures controlling access to those keys. In a container context, these requirements should be met by leveraging the key management and secrets management capabilities available through orchestration platforms such as Kubernetes, Docker EE, Red Hat OpenShift and others.
An advanced protection would be to monitor network transmissions with DLP (data loss prevention) capabilities to detect unencrypted cardholder transmissions.
4) Encrypt transmission of cardholder data across open, public networks (PCI DSS 4.1)
Organizations must use strong cryptography and security protocols to protect cardholder data during transmission over open networks, ensuring that only trusted keys and certificates are accepted and protocols only support secure versions or configurations. Also, unprotected primary account numbers (PANs) must never be sent using common messaging technologies such as email, instant messaging, SMS, chat, etc. To address this requirement, firewalls protecting containerized environments must be able to automatically whitelist SSL/TLS connections while blocking all unencrypted or unauthorized connections, as well as those from messaging technologies.
To verify continual compliance, an advanced protection would be to monitor network transmissions with DLP capabilities to detect unencrypted cardholder transmissions.
5) Protect all systems against malware and regularly update antivirus solutions (PCI DSS 5.1, 5.2)
Antivirus solutions must be deployed on all systems commonly affected by malicious software, such as PCs and servers. These solutions must be well-maintained, remain active and be impossible to disable or alter unless authorized by management (and then only on a specific and limited basis). Organizations can use orchestration tools to ensure that security containers are always running, along with a container firewall designed to virtually patch and keep systems up-to-date while continuing to detect suspicious file system activity.
Modern cloud-native environments are moving toward a ‘zero-trust’ declarative security approach, where the behavior of each application is characterized and locked down. This reduces the false-positives and lack of timely updates of traditional anti-malware systems while increasing the protection in run-time.
6) Develop/maintain secure systems and applications (PCI DSS 6.1-6.7)
PCI-DSS compels organizations to apply attentive care to securing all relevant systems and applications throughout their development and into production. This means actively addressing security updates and newly discovered vulnerabilities and following prescribed rules for change control processes and procedures. For those utilizing container environments, this means employing a container security strategy that protects applications throughout the entire build-ship-run cycle. Container security integrations into CI/CD environments are ideal for addressing these needs.
7) Restrict cardholder data access on a need-to-know basis (PCI DSS 7.1-7.3)
The only individuals within an organization who should have access to cardholder data are those who need it to do their jobs. PCI DSS compliance requires organizations to establish access control systems that enforce such restrictions. To achieve this, businesses should utilize security systems that integrate with role-based access controls (RBACs) offered by Kubernetes, OpenShift and others, as well as enterprise application protocols such as LDAP and Active Directory (AD). Actual cardholder data should never be exposed to security and DevOps teams who are monitoring the environment.
8) Identify and authenticate access to system components (PCI DSS 8.1-8.8)
User identification management—complete with unique IDs and effective authentication methods—are required by PCI DSS. All individual administrative and remote access to the CDE must also be secured by multi-factor authentication. Using RBACs, enterprise LDAP/AD or other protocols such as SAML, SSO or OAuth can provide these security measures.
9) Track and monitor all access to network resources and cardholder data (PCI DSS 10.1-10.9)
PCI DSS requires the implementation of audit trails to reconstruct all access to system components by each individual user, along with the specific details of each event. These audit trails must also be secured such that they cannot be altered, and all logs and security events must be reviewed to recognize anomalies or suspicious activity. Organizations utilizing containers should implement security systems that maintain an event log of all user activity and actions, track all communications between containers for event reconstruction and offer compatibility with SIEM systems.
10) Regularly test security systems and processes (PCI DSS 11.1-11.6)
PCI DSS compliance requires running network vulnerability scans quarterly (at minimum) and after any significant network changes. Network intrusion detection and/or prevention techniques must be used along with traffic monitoring at the perimeter and at key points within the CDE. Change detection mechanisms providing alerts on any unauthorized modification of critical files are also requisite. From a container environment standpoint, it’s important to use a firewall that actively scans running containers for vulnerabilities and threats both within and at the perimeter of the environment, to automatically detect and mitigate all suspicious behavior or intrusions.
By ensuring the correct protections are in place to safeguard containerized environments in real-time and in accordance with PCI DSS requirements, enterprises can better achieve (and maintain) thorough compliance while confidently taking full advantage of what microservices and containers offer.



