GitLab Offers CI/CD Platform as Hardened Container Image
GitLab is making available an instance of its namesake continuous integration/continuous delivery (CI/CD) platform in the form of a hardened container image that can be downloaded via an Iron Bank repository set up by the U.S. Department of Defense (DoD).
Joe McKairnes, federal solutions architect for GitLab, says Iron Bank has become the central repository through which the federal government is sharing artifacts with not only other federal agencies but also contractors and suppliers. That capability reduces the time it takes for IT teams in the federal government to get contracts approved to days from months, he says.
Artifacts that are housed in the Iron Bank repository are scanned for vulnerabilities as part of a larger DoD initiative to promulgate adoption of best DevSecOps processes, McKairnes says. Any vulnerabilities that are discovered after an artifact is included in the Iron Bank repository are also required to be remediated.
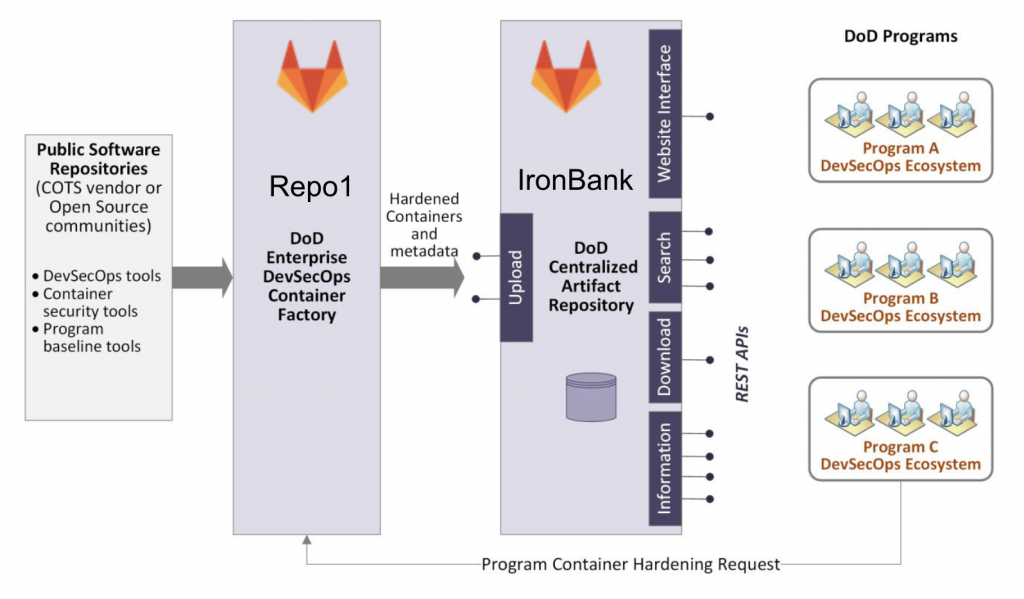
Iron Bank is the DoD repository of digitally signed, binary container images that have been hardened according to the Container Hardening Guide defined by the DoD. DevOps across the DoD are being encouraged to check if the container images already exist in Iron Bank, also known as the DOD Centralized Artifacts Repository (DCAR), and only use DoD signed containers whenever possible.
The DoD also makes available a DevSecOps Platform (DSOP), a collection of approved Kubernetes distributions, infrastructure as code playbooks and hardened containers that comply with a DoD Enterprise DevSecOps Reference Design. DSOP source code is hosted on a DoD Centralized Container Source Code Repository (DCCSCR), also known as Repo One.
The U.S. Air Force has been at the forefront of much of the adoption of best DevOps practices with the DoD via initiatives to create software factories such as Kessel Run, LevelUP, Kobayashi Maru, SpaceCAMP and BESPIN.
Of course, entities that develop software in collaboration with federal agencies will also be required to adhere to best DevOps practices being defined across the DoD. Over time, the influence the DoD is likely to have on the adoption of best DevSecOps in both the public and private sectors is considerable.
While containers have been a major boon to software development by encouraging reusability, organizations inside and out of government agencies are paying a lot more attention to how containers are shared among development teams as software supply chain concerns continue to rise. There already have been plenty of incidents in which unwanted applications have been inserted into containers residing on repositories such as Docker Hub. As a result, many DevOps teams are building their own repositories to share container images more securely.
Longer-term, it’s clear development of containerized applications will revolve around repositories. As that trend accelerates, it creates an opportunity to centrally apply everything from security scans to compliance checks to ensure the integrity of the software supply chain. The challenge, of course, is going to be getting everyone to employ only the officially sanctioned repository to download container images.