Sysdig Employs AI to Thwart Container Cryptojacking Attacks
At the Black Hat USA 2022 conference, Sysdig today revealed it is adding machine learning algorithms capable of detecting cryptojacking attacks to its cloud service for securing container applications. The algorithms are offered at no additional charge, Sysdig says.
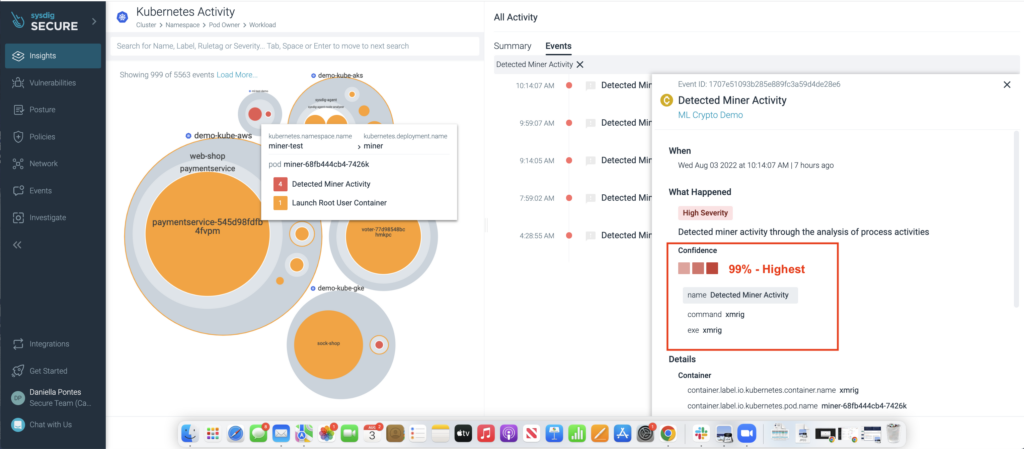
Daniella Pontes, senior manager for product marketing at Sysdig, says the cloud detection and response (CDR) capabilities—in combination with its existing threat engine—can block cryptojacking in the cloud with 99% precision.
Initially viewed as a nuisance crime, cryptojacking involves cybercriminals surreptitiously stealing compute resources in the cloud to mine cryptocurrencies. But the cost of these attacks has now skyrocketed, and it is not uncommon for organizations to see bills for $100,000 to $500,000 in a single month as a direct result of cryptomining activities, notes Pontes. Those costs can be especially high when graphical processor units (GPUs) are used to mine cryptocurrencies, she adds.
The challenge is that cybercriminals have become especially adept at evading most existing cryptojacking detection techniques. Rather than looking for a specific type of cryptomining attack, Sysdig is now using machine learning algorithms to identify behavior and patterns that are unique to a cryptomining process. Once detected, that process is automatically blocked regardless of whether it is a known form of a cryptomining attack or some type of new method being employed, she says.
Cryptomining attacks can also lead to more lethal attacks being launched later, if they’re not identified early and stopped. It’s not uncommon for purveyors of cryptomining attacks to resell the techniques they employed to compromise an IT environment to other cybercriminals looking to, for example, launch a ransomware attack by embedding malware in a container that is then embedded within a cloud application.
It’s increasingly clear that cloud services will play a much larger role in securing application environments. A cloud service enables a vendor to collect enough data to effectively train machine learning algorithms and artificial intelligence (AI) models. Of course, AI models are not going to replace the need for cybersecurity professionals any time soon, but they do provide a level of augmentation that is critical as application environments become more complex. There are simply not enough cybersecurity professionals available with the expertise required to secure modern application environments based on containers that are frequently ripped and replaced.
Of course, the hope is that more responsibility for application security will be shifted left toward developers themselves. However, not every developer is going to have the same level of cybersecurity expertise. In fact, it may still be years before most developers attain the level of cybersecurity expertise required to effectively secure application environments.
The only way to bridge a growing cybersecurity gap will be to rely more on AI models, noted Pontes. However, there is no silver AI bullet for cybersecurity, she added. Each AI model needs to be tuned for a specific use case that lends itself to be automated, noted Pontes.
It may be a while before AI is considered just another standard cybersecurity capability but it’s already apparent that most developers and cybersecurity teams need as much help as they can get regardless of whether is comes from another human or machine.