Nirmata Delivers Cloud-Native Policy Management Platform
Nirmata today announced general availability of the Nirmata Cloud Native Policy Management platform based on a Kyverno policy engine that runs natively in Kubernetes.
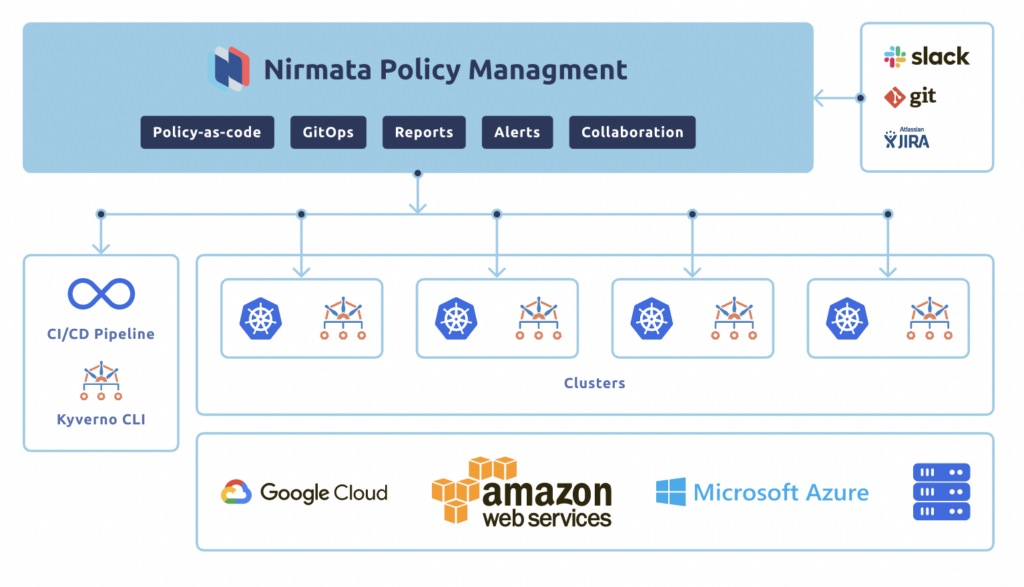
Ritesh Patel, vice president of products for Nirmata, says Nirmata Cloud Native Policy Management provides a platform through which IT teams can easily create what the company calls Intelligent Guardrails for managing compliance and security based on code.
Kyverno was originally developed by Nirmata, and has emerged as an alternative to the Open Policy Agent (OPA) for managing compliance-as-code. It is a declarative policy engine that runs as an admission controller that can validate, mutate and generate any configuration data based on customizable Kubernetes policies. It also differs from OPA in that it does not require IT teams to learn a programming language to implement it.
Today, Kyverno is a sandbox-level project being advanced under the auspices of the Cloud Native Computing Foundation (CNCF). Nirmata claims Kyverno has been downloaded more than 7 million times. OPA, meanwhile, is a graduated open source project that is also being advanced within the CNCF alongside Kubernetes and other tools that have attained graduated status.
Patel says Nirmata Cloud Native Policy Management makes it possible to centrally manage Kyverno in a way that makes it easier for IT teams to identify, fix and prevent workload and cluster misconfigurations. That approach makes it easier for IT teams to implement DevSecOps best practices via a platform to manage policy life cycles in complex cloud-native application environments made up of microservices that each need to be individually secured, notes Patel. IT teams can also employ curated and crowdsourced policy sets provided by Nirmata to better secure Kubernetes clusters.
Most Kubernetes clusters today are provisioned by developers that typically have limited cybersecurity expertise. As such, the odds that a Kubernetes cluster—arguably one of the most complex IT environments in use within enterprise IT environments—is misconfigured is high. Ultimately, the goal is to reduce risks by preventing configurations that don’t comply with a wide range of compliance mandates, adds Patel.
Less clear is the degree to which compliance concerns are holding up deployments of Kubernetes clusters in production environments. Regulated industries tend to have a higher compliance bar, but as privacy regulations continue to be rolled out around the world more organizations are finding they now need to address a number of compliance requirements. A policy-as-code approach allows DevOps teams to programmatically implement compliance controls before any application is deployed in a production environment.
Much like security, responsibility for compliance is increasingly being shifted left toward developers. Security and IT teams will still define the controls that need to be implemented, but increasingly it will be developers that make sure those controls are actually embedded within an application. In theory, at least, the number of instances where organizations are cited for compliance violations should, over time, steadily decline. The challenge, of course, is making it as simple as possible to implement those controls at a time when most developers are already hard-pressed to meet application development deadlines.