Anchore Updates Container Security Platform
Anchore has updated its container security platform as part of an effort to enable organizations to better secure software supply chains that include Kubernetes clusters.
Neil Levine, vice president of products for Anchore, says Anchore Enterprise 3.0 makes it possible for developers and cybersecurity teams to ascertain the security status of container images as they are running.
Anchore Enterprise can also run automated security checks both locally on developer tools and across a continuous integration/continuous delivery (CI/CD) pipeline. Lightweight tools that can be deployed at various points in the software development life cycle feed results back to the central Anchore Enterprise system; those results are then compared to policies defined by a cybersecurity team.
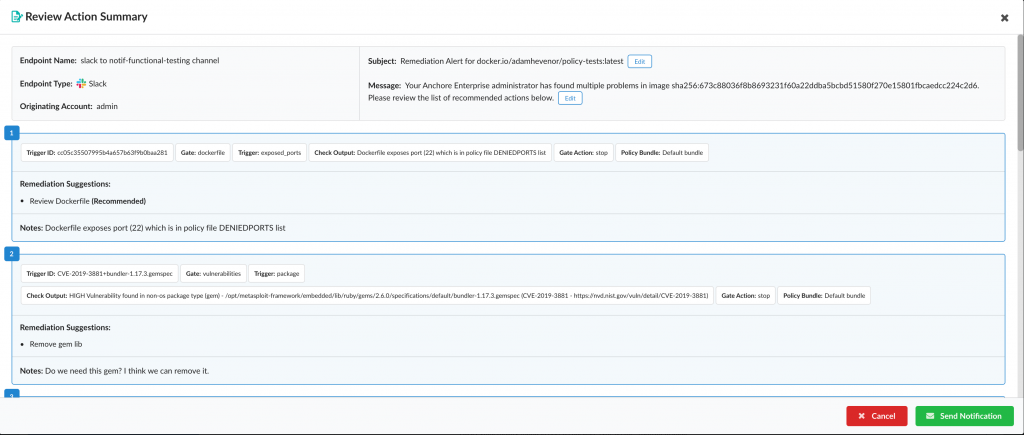
The latest edition of Anchore Enterprise 3.0 now also provides automated remediation suggestions for vulnerable containers that can be shared via DevOps tools such as Jira, Slack, Teams, Gitlab, GitHub, traditional email and more.
Finally, Levine says Anchore Enterprise 3.0 also reduces the number of false positives generated. Users can now easily correct any misidentifications to ensure that future checks have fewer false positives. In addition, security teams can set up time-based allow lists that eliminate the need to generate repeated alerts when, for example, an exception to a policy has been made.
In general, Levine says, it’s apparent that Kubernetes security needs to be addressed within the context of a software supply chain in the wake of recent high-profile breaches.
Cybersecurity teams in general are now applying a deeper level of scrutiny to the way software is constructed and deployed, Levine adds. That shift requires an approach to DevSecOps that goes beyond simply scanning containers for vulnerabilities and securing the runtime environment they are deployed on, says Levine.
At present, the level of DevSecOps adoption between – and even within – organizations tends to vary widely. Organizations of all sizes are reexamining their software development life cycle (SDLC) processes with an eye toward making sure that malware can’t be introduced anywhere in the process. That shift will require deeper integration between container security tools and the CI/CD platforms that drive SDLC in most modern enterprises, Levine says.
While awareness about the need for DevSecOps has increased, most organizations are still a long way from deeply embedding security within their application development toolchain. Developers are generally open to embracing DevSecOps, so long as it doesn’t slow down the application development process. Cybersecurity teams, however, will want to be able to validate that the proper controls are in place before an application goes into a production environment.
Of course, building applications faster only to see them fail a security check just before deployment defeats the purpose of embracing DevOps in the first place. The only way to truly accelerate application development is to make sure security issues are addressed as early in the application development process as possible. Otherwise, application workloads will be rolled back either just before deployment or, worse yet, after.